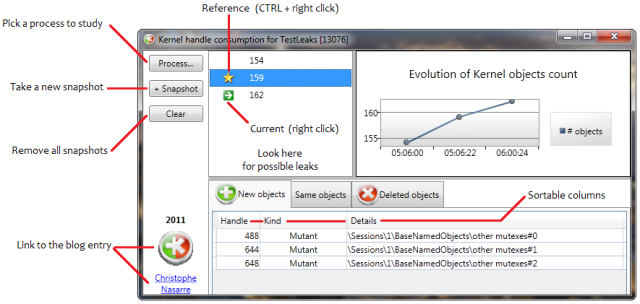
Download Kernel Leak Shell v1.1
The original version of Kernel Handle Leaks Shell has a frustrating feature: you have to explicitely start it elevated or the same error message will pop up all the time
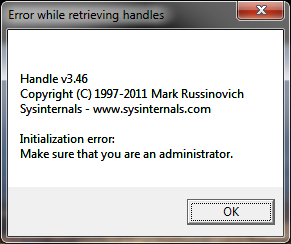
because handle.exe that it executes behind the scene will not have the required privileges.
An UAC discussion is far beyond the scope of this post but feel free to read the related pages in chapter 4 of Windows via C/C++ for a complete coverage.
If you don’t want to right click on the executable and pick the Run as administrator item all the time
you could use Windows shortcut settings.
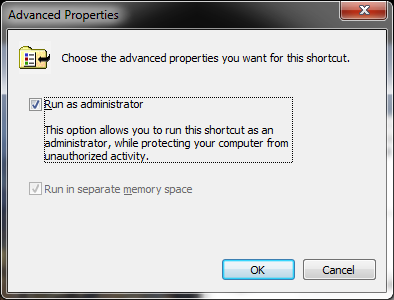
You have two choices: either via the Compatibility tab
or via the shortcut tab
Both solutions are working and you’ll always get the elevation prompt. Note however that the icon won’t show the elevation shield official UI hint.
 |
expected UI hint 
|
So… How to let the tool be automatically elevated by Windows when it starts and get a nice shield hint?
As explained in Create and Embed an Application Manifest (UAC), the answer is simple: you need to associate/embed a manifest with the right information to the executable. Unlike what is detailed in the MSDN page, the embedding process becomes really easier with Visual Studio 2010 because you don’t need to mess up with post build step in order to call mt.exe.
First, you add a manifest to the application if not already there. Right click on the project and Add|New Item…|General|Application Manifest File

Second, set the requestedExecutionLevel.level attribute to “requiredAdministrator” instead of the default “asInvoker”.
Third, build the application. And… That’s it!
I hope this helps